This help topic has general information about the feature and its configuration. For detailed configuration information, please refer to the Shop Floor Time SSO with SAML Configuration Guide.
You can configure Shop Floor Time for Single Sign On (SSO) authentication with a protocol called SAML 2.0 (Security Assertion Markup Language).
SAML 2.0 uses security tokens containing assertions to pass information between the user, an Identity Provider, and a Service Provider. The Identity Provider vouches for the user who is logging in. The Service Provider provides services to the user.
When a user accesses the Shop Floor Time application, the user is redirected to the Identity Provider, and logs in using their Identity Provider credentials. You can also have users access the Identity Provider directly. Next, the Identity Provider authenticates the user and sends a response to the Service Provider. The Service Provider verifies the user and logs the user in to Shop Floor Time. The user is redirected to an authenticated session of Shop Floor Time.
To use this feature, you will need to configure the Service Provider and Identity Provider.
The Service Provider configuration is covered in detail in the Shop Floor Time SSO with SAML Configuration Guide. The Service Provider configuration will depend on what type of application server you are using for Shop Floor Time – JBoss/Wildfly or WebLogic. If you are using JBoss/Wildfly as your Shop Floor Time application server, then you must use Keycloak for the Service Provider configuration. If you are using WebLogic as your Shop Floor Time application server, you must configure the Service Provider in the WebLogic Administration Console.
The Identity Provider configuration will depend on which Identity Provider you are using (Ping Identity, Okta, etc.). You will have to consult the Identity Provider's documentation for configuration steps.
SSO Configuration with SAML is available for the web application and the Mobile Web Application. It is not available for the native Mobile Client app.
Note that you can also configure Shop Floor Time to connect/communicate with a Kerberos server for SSO authentication. See SSO Policy for more information.
See Also:
SAML SSO Log In/Log Out Example
use_external_sso
You will need to change the Application Setting called use_external_sso to TRUE. This setting can be configured for the MOBILE and WEB applications.
When use_external_sso is TRUE and a person accesses the Shop Floor Time URL, the person will be redirected to the Identity Provider login page and be able to log in using their SSO user name and password (provided the necessary Service Provider and Identity Provider are running).
In addition, the Log In and Manual Log In buttons will appear when the user logs out of Shop Floor Time and use_external_sso is TRUE. The Log In button will log the person back into Shop Floor Time without having to enter their SSO username and password. The Manual Log In button displays the regular Shop Floor Time Log In page.
If use_external_sso is TRUE, you can also specify an external_sso_logout_url which will appear instead of the Log In page when the user logs out of Shop Floor Time.
external_sso_logout_url
You can use this setting to define a URL that will display when users log out of Shop Floor Time, instead of displaying the Log In page. For example, you may want to direct users to your company web site, or a page that instructs them to closer the browser to fully log out. This URL will only display when use_external_sso is TRUE.
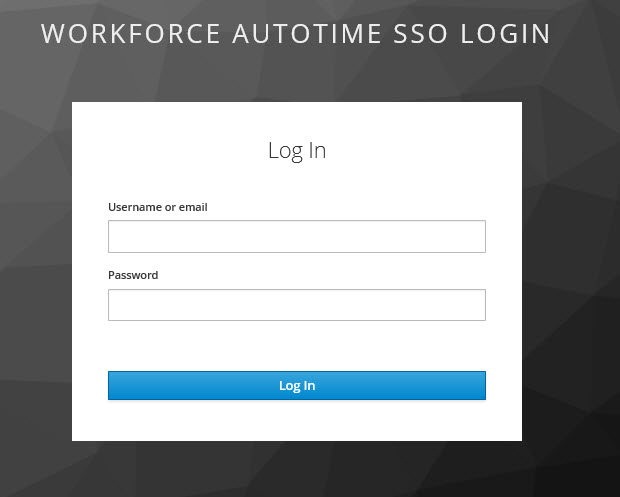
In this example, the user accesses the Shop Floor Time URL, http://localhost:8080/autotime, and is immediately redirected to the Identity Provider (http://localhost:8180/auth/realms/wat_saml_realm/protocol/saml/clients/AutoTime). You can see this web site address in the browser window. In the example below, the Identity Provider is a Keycloak server.

The user logs in with the credentials used for the Identity Provider. For example, in some companies, employees use an email address and network password for Single Sign On.
After the user clicks Log In, the Shop Floor Time application opens and the person is logged in.
When the person logs out (provided there is no external_sso_logout_url setting configured), the Shop Floor Time Log In page displays options to log back in or manually log in.
The Log In button logs the person back into Shop Floor Time without entering a user name or password.
The Manual Log In button displays the regular Shop Floor Time Log In page, where the person must use a Shop Floor Time user name and password to log into the application.